
As I was preparing for my CEH certification, an IoT module appeared in the v11 version. As a result, I will attempt to give this article an overview of the selected solutions and, in addition to this, I will discuss how we can ensure confidentiality in systems
This text will also cover the security of systems at the network layer and the dangers of using radio waves as a transmission medium. On top of that, you will learn what types of open-access systems attacks you might encounter daily. You may also be interested in my previous article: Internet of Things security – encryption protocols in IoT systems.
IoT, or the Internet of Things (alternatively, in some publications, the Internet of Everything), is a field in information technology that dates back to the early 80s. Here in Poland, we have a saying, “When something serves everything, it does nothing.” In this context, such a description of IoT would be highly unfair.
In a nutshell, IoT devices not only live up to their names by providing solutions for human activities (from industrial automation to medical and life-saving devices, to alarm sensors, to CCTV cameras, to smart TVs), but they also come with networking modules. It does not matter whether the NIC (network interface) is wired or wireless because, in any case, it enables communication within broad networks, including the internet. This method allows systems to communicate and be controlled from the top down, and a gateway (IoT gateway) is used to detach them from the internet. IoT devices benefit from connectivity and can be controlled via applications, and elements of such systems often include cloud servers where data analysis is performed. The range of applications for IoT systems is extremely extensive, and as a result, severe security issues with the Internet of Things can arise.
Network layer security mechanisms and technologies that can provide for network segmentation, i.e., splitting the network into separate VLANs (segmentation at the L2 layer), come to the rescue. A significant added value for the security of such systems will be a NAC policy based on the radius server and the 802.1X standard in general.
To systematize this information, I will use a general diagram of the architecture of such systems:
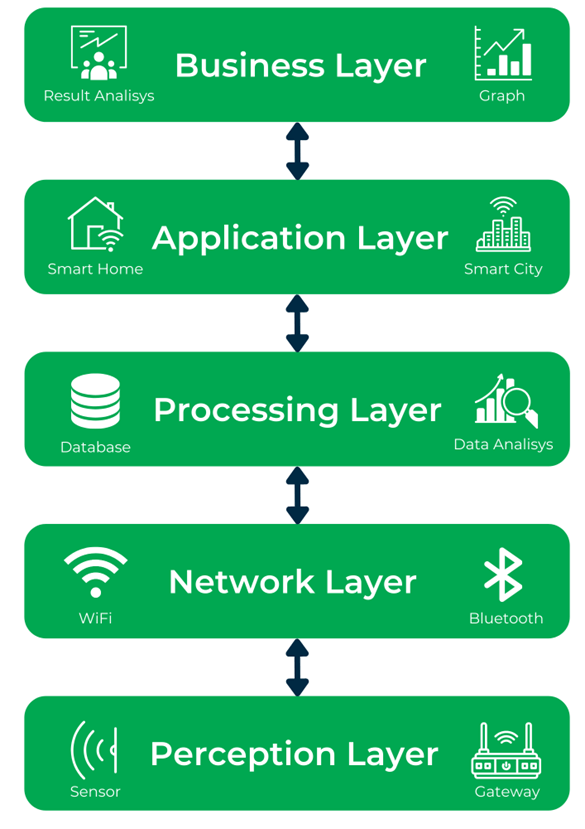
In IoT systems, we may often encounter low power consumption requirements, so that battery power lasts as long as possible (for example, in systems such as ZigBee). Unfortunately, a trade-off must be made here, as encryption algorithms can sometimes be greedy for computational resources – especially asymmetric ones (multiplication, i.e., several multiplications, multiplication of points on elliptic curves, i.e., multiple additions) are computationally expensive and correlate with power consumption.
Since I am a huge chess fan, I feel inclined to quote a joke by one of Poland’s strongest chess grandmasters, Bartosz Soćko. Reflecting on the power of computers in the face of human capabilities in this discipline and the resulting dangers in the form of electronic doping, he concluded by saying that modern grandmasters have to work hard not to lose to a coffee grinder. Hearing this joke immediately brought to mind the ubiquity of IoT devices. In some fields, relatively low computing power can already challenge the human intellect! But let’s cut to the chase.
The use of wireless communications brings with it the serious risk that it is impossible to hide a system that is present in the frequency spectrum. It stands to reason that these systems are susceptible to eavesdropping, and consequently, eavesdropped communications are vulnerable to reverse engineering (e.g., cryptanalysis). Radio systems at the functional layer rely on modulation techniques and information theory – the person who analyses them must also be proficient in these matters.
Here are the tools available for analyzing the firmware itself. There are specialized instruments (spectrum analyzers, oscilloscopes) available that can help to find so-called side channels. Essentially, these techniques involve observing the device during regular operation. Several parameters are taken into account, including power consumption, heat emission, and electromagnetic radiation.
A deliberately disrupted operation of the IoT device under investigation can, however, yield outstanding results. For instance, when we start to interfere with the device’s clock signal (these approaches are generally referred to as Fault Injection Attacks), attempts are made to unlock the JTAG (glitching). Once the JTAG interface is unlocked, a gateway opens to allow us to manipulate the embedded software. Observing the device waveforms reveals most software-based mechanisms that ensure the device’s security under test. To make it even more complicated, various types of shielding coatings are used (incorporated into the design of the device during assembly) to weaken the emitted electromagnetic field through this side channel.
Physical protection alone (flooding with epoxy resin or hiding address lines between electronic components) can help to prevent physical access to the printed circuits. Using reverse engineering to test a system’s resistance to the types of attacks mentioned above is one way to secure an IoT system.
In this case, a graph of the dependence on power consumption as a function of time is created during the execution of the ciphertext. Ultimately, this leads to the core. In the SPA (Simple Power Analysis) approach, RSA-based systems, which rely on a factorization technique at the functional layer, show vulnerability to this type of analysis. A solution to this problem is to throw a potential attacker off the trail by using techniques such as active masking of the input data, e.g., randomly delaying it and adding the processing of redundant elements.
On the other hand, attempts are made to extract the key in the DPA (Differential Power Analysis) approach, using statistical analysis on a set of measurements of the cryptographic system under study (during its operation). Regarding security techniques, there are several libraries available on the market that can eliminate this risk. Still, there are hardware-based solutions that prevent this type of attack.
Here you will find an example of research into a market-leading and recognized security – the AES symmetric algorithm.
To conclude, it is worth mentioning two models that help to introduce information security policies in organizations: the CIA triangle and Parker’s Hexagon.
CIA stands for three things:
This model was expanded in 2002 by Donn B. Parker with the following elements:
The state of ownership is closely related to free access. It is, therefore, easy to imagine a situation where a device comes with sophisticated and non-trivial security features, only to have them destroyed by such a mundane action as manually resetting it to default settings.
IoT is a field experiencing very rapid market share growth. Many sources deal with manufacturing standards and guides for effective practices to secure them. The threats lurking in the security of IoT devices and their protection are numerous – the points I have presented are not exhaustive. Still, they are a helpful starting point for a discussion; one I strongly recommend.
